Blog
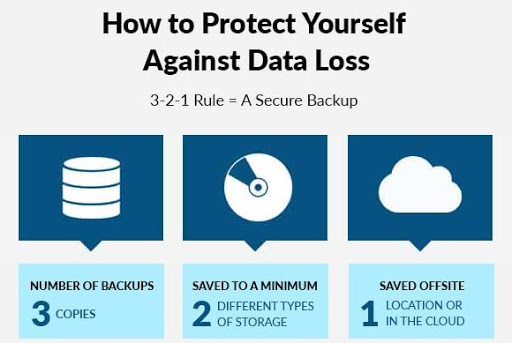
Backup is King
Everyone should backup their data, especially for a business. Unforeseen events happen and no matter how much you pray, wish or deny, failures happen. I believe in the 3-2-1-0 Rule, regardless of Operating System, Manufacture or Support Contract. This approach helps to answer two important questions: how many backup files should I have and where…

Our privacy is once again being trampled on.
The US Senate recently passed a bill to extend elements of the Patriot Act. Notably, this legislation included parts that would increase the FBI and CIA’s ability to legally access your browser search history without a warrant. The age-old argument that’s often trotted out when government power is expanded to trespass on individual privacy is…

Review of the Surface Book 3
I used to work with Scott Hanselman, way back in the day. He now works at Microsoft as a Technology Evangelist. His blog is not only a great resource, but a wealth of knowledge for the development community. Go to his link for a deep dive into the Surface Book 3. My assessment of the…

Security Update May 8th – Our First Responders are under ATTACK
Once again our protectors against COVID-19 are under attack. A new malicious spear-phishing campaign once again using the COVID-19/coronavirus pandemic as a lure. This latest email campaign targets a medical device supplier, wherein the attacker is inquiring about various materials needed to address the COVID-19 pandemic due to the high demand for supplies. It includes…

Weekly Security Update – May 1st
Ransomware has been a dominant threat to organizations for several years now, causing damage estimated to be in the billions of dollars. Increasingly, a common action carried out by ransomware attacks is to erase the volume backups (i.e., shadow copies), thereby preventing victims from being able to recover any files that had been encrypted. Defenders…

Anti-Virus programs. How effective are they really?
Many people don’t realize that Anti-Virus programs are not 100% effective. They don’t catch the viruses when they are accidentally downloaded, notify you that you have been infected after the fact, or goes crazy on a legitimate application, such as Excel. This is why I have always recommended that Anti-Virus and Malware protection be layered.…

Even your smartphone can get viruses and malware
Is your iphone or android phone protected against viruses and Malware? Most individuals do not properly protect their phone, like they would if it is a computer. Many people believe that phones can’t get viruses, malware or even be hacked. They can! Black Rose Lucy ransomware tries to scare victims into paying a ‘fine’ –…

How safe is ZOOM?
A new Zoom flaw lets hackers record Zoom meeting sessions and to capture the chat text without the knowledge of meeting participants’ even though host disables recording option for the participants. https://gbhackers-com.cdn.ampproject.org/c/s/gbhackers.com/zoom-malware/amp/

SEP end of life is coming. What are your options?
It took everyone by surprise—Symantec will no longer sell or support their popular SEP products, with an official end-of-life date set for Nov. 2, 2020. Here’s the good news: Your customers are eligible for a free upgrade if they hold a current valid subscription for Symantec Endpoint Protection Cloud (SEP C) or Symantec Endpoint Protection…
