Blog
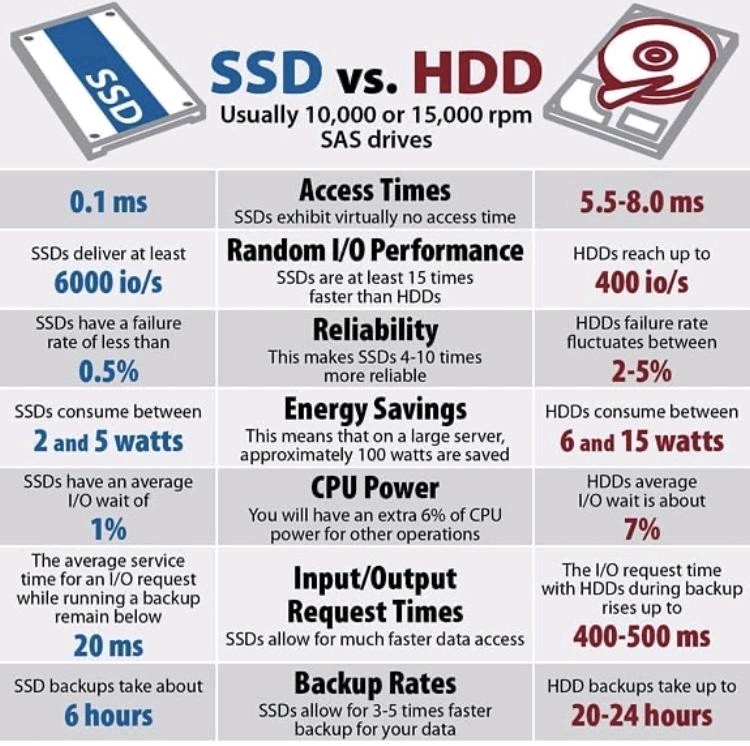
To Spin or Not to Spin, that is the question.
This is a great example of the differences between a solid state (SSD) and a traditional hard drive. As you can see the access time, IOPS and performance of the SSD is far better. Really, it is the difference between night and day. The cost of SSDs are far more reasonable than 5 years ago.…

Why Cyber-security is Important
John Ford, ConnectWise Chief Information Security Officer, put together a quick little video to explain what a Cyber Attack is and how it impacts your business. Your work life and personal life are not separate. Everyone checks their work email on their phone. Everyone looks at Facebook at work or check their personal email at…
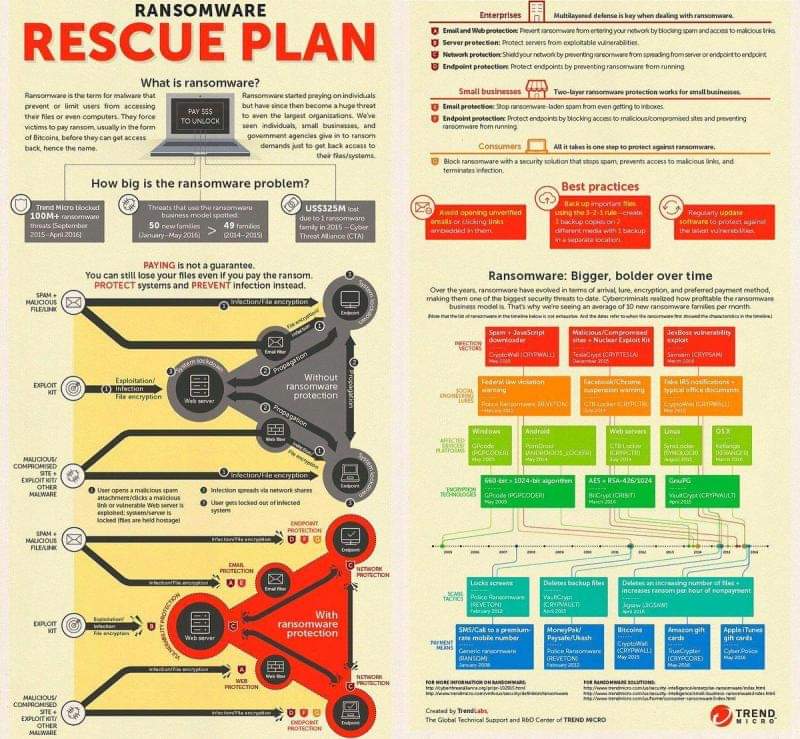
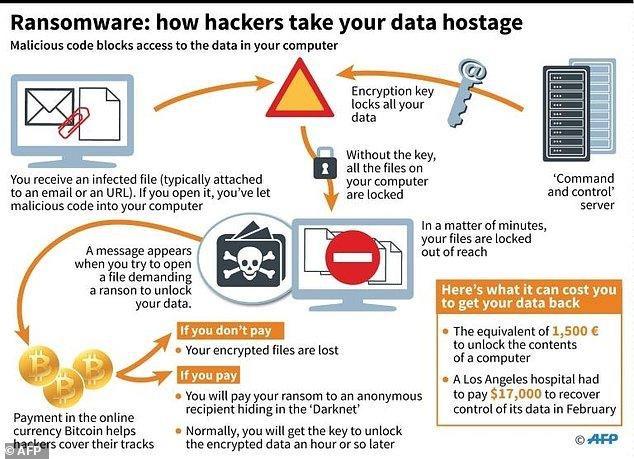
Do you have a Rescue Plan In the event of a Malware Infection?
Let us perform a security analysis of your company – Today! Does your company have a rescue plan? Some malware is planted days or even weeks before being activated, making backups useless. So, what’s the Plan, Stan?

Encryption People.. Encryption…
Tesco, a giant supermarket club in England, similar to Costco in the US, announced that 600,000 names and passwords were stolen. The thief made off with the company’s database. It is known that the data was used to gain access to other websites. None of the company’s financial data was accessed. But… Who cares about…

Best Anti-virus Software in 2020
I was a bit surprised about some of the rankings. I have used ESET, SEP and Norton in the past. I can see why they ranked where they did. These big names are good at what they do, but there is a lot of bloat in these products. I would like to test out BitDefender…

Most common forms of cyberattacks last year
New research from BlackBerry Limited shows hackers use different strategies and attack types, depending on the industry they’re targeting. For example, criminals targeting the technology and software industry are most concerned with stealing intellectual property. To that end, a quarter of attacks (26 percent) were ransom based. Healthcare organizations also encountered a high proportion of…

US Railroad reports data breach AFTER a Ransomware Attack
A US Railroad company, RailWorks Corporation, reported a data breach after a Ransomware attack occurred. The exposure 3,500 Personal Identifiable Information (PII) of their employees (current and former), dependents and beneficiaries. Not only did RailWorks have to deal with the RansomWare, but also the exposure of a data breach of PII information of their employees.…

The Agency in charge of security for the White House gets Hacked.
“It’s a painful irony that the agency charged with providing secure comms for the White House has fallen victim to a data breach.” The hack also could have grave implications for the upcoming presidential election, especially with the memory of Russian interference in 2016 still fresh in many minds. There already has been evidence that…